Difference Between MAC Address and IP Address
MAC Address vs IP Address – Difference Between Them
- MAC address is assigned by the manufacturer of the hardware interface, while the IP address is assigned by the network administrator or Internet Service Provider (ISP).
- MAC address is a unique hardware identification number that is assigned to a NIC (Network Interface Controller or Card), whereas the IP address is an address that helps you identify a network connection.
- MAC addresses define the identity of the device, but IP addresses describe how the devices are connected to the network.
- MAC addresses can be used for broadcasting, on the other hand, IP addresses can be used for broadcasting or multicasting.
- The MAC address is implemented in the Data-Link layer of the OSI or TCP/IP reference model. In contrast, the IP address is implemented in the network layer of the TCP/IP or OSI model.

Here, I have analyzed the difference between MAC Address and IP Address and will comprehensively evaluate their pros and cons.
What is a MAC address?
MAC address is a unique identifier that is assigned to a NIC (Network Interface Controller/ Card). It consists of a 48-bit or 64-bit address, which is associated with the network adapter. MAC address can be in hexadecimal format. The full form of MAC address is the Media Access Control address. A MAC address is generally six sets of two-digit characters that are separated by a colon.
What is an IP Address?
An IP address an address that helps you identify a network connection. It is termed the ‘Logical Address,’ which is provided to a connection in a network.
IP addresses help you control how devices on the Internet communicate and define the behavior of internet routers.
Difference Between MAC Address and IP Address
Here are the main differences between MAC and IP addresses that I’ve come to understand:

| Comparison Basis | MAC Address | IP Address |
|---|---|---|
| Definition | MAC address is a unique identifier that is assigned to a Network Interface Controller/ Card. | An IP address is an address that helps you identify a network connection. |
| Full Form | The full form of MAC address is Media Access Control Address. | The full form of an IP address is an Internet Protocol Address. |
| Assigned by | It is assigned by the manufacturer of the interface hardware. | It is assigned by the network administrator or internet service provider (ISP). |
| Send By | Information is send by Ethernet using the MAC address. | Information is send by the Internet using the IP address. |
| Filter | The MAC filtering feature helps to prevent security threats by hackers. | The IP address does not have any specific filters. |
| Defines | MAC defines the device identification. | IP addresses define how the devices are connected to the network. |
| Seperated By | MAC address is separated by a colons. | IP address is separated by dots. |
| Type | MAC address is hardware oriented. | IP address is software oriented. |
| Feature | You can’t hide the MAC address from the device. | It is possible to hide IP addresses using a router or VPN. |
| Flexibility | The MAC addresses are not flexible and not remain constant for a device. | The IP address is flexible. It gets changed every time whenever it connects to some other network. |
| Identify the Device | MAC address helps you to identify the device in the local network. | IP address helps you to identify the device in the global network. |
| Used for | MAC addresses can be used for broadcasting. | The IP address can be used for broadcasting or multicasting. |
| Layer | The MAC address is implemented in the Data-Link layer of the OSI or TCP/IP reference model. | The IP address is implemented in the Network layer of the TCP/IP or OSI model. |
| Solve | MAC address help to solve IP address issues. | IP never addresses able to solve MAC address issues. |
Why need MAC address?
Reflecting on my usage, here are the primary benefits of employing MAC address:
- It provides a secure way to find senders or receivers in the network.
- MAC address help you prevent unwanted network access.
- MAC address is a unique number; hence it can be used to track the device.
- Wi-Fi networks at the airport use the MAC address of a specific device to identify it.
Why need an IP address?
Here are the advantages I’ve found with using an IP address:
- An IP address is assigned to every device on a network so that the device can be located on that network.
- It helps you develop a virtual connection between a destination and a source.
- IP address is one type of numerical label assigned to each device connected to a computer network
that uses the IP for communication. - It acts as an identifier for a specific machine on a particular network.
- It helps you specify the technical format of the addressing and packaging scheme.
Characteristics of MAC Address
From what I’ve seen, here are some essential characteristics of MAC addresses:
- TCP/IP networks can use MAC addresses in the communication.
- It helps you to Identify a specific NIC in a computer on a network.
- Network devices cannot efficiently route traffic using MAC addresses.
- Not provide information about physical or logical network configuration.
Characteristics of IP Address
Based on my findings, a key characteristic of an IP address is:
- IP address is a numeral label assigned to each device.
- IP helps you control how devices on the Internet communicate and identifies the behavior of internet routers.
- It is assigned by the network admin or internet service provider (ISP).
- It can be either 32-bit long (4 bytes) or 128-bit (16 bytes).
How to find out your IP address?
Here is a way to find the IP address in Windows:
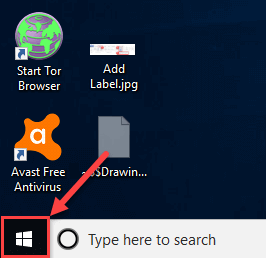
Step 1) Click on the “start” button.
Click on the Start Menu Icon.
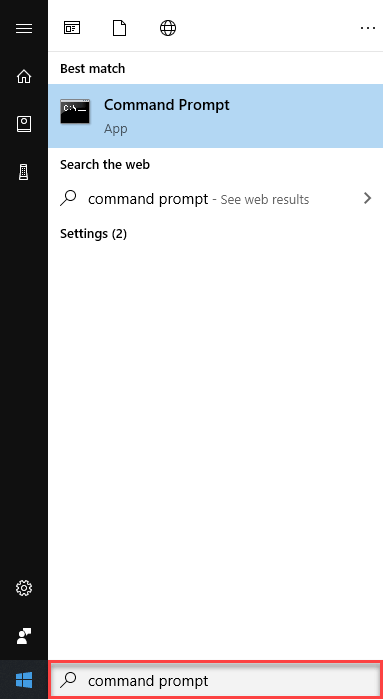
Step 2) Type the command prompt in a “search” box.
Click on the search result.
Step 3) In the command prompt type ipconfig and press enter. You can see a field called IPv4 Address.
How to find your MAC address?
Here is a way to find the MAC address in Windows.
Step 1) Click on the “start” button.
Click on Start Menu Icon
Step 2) Type command prompt in a “search” box.
Click on the search result.
Step 3) In the command prompt.
Type ipconfig /all and press enter.
Step 4) Output of the command is shown.
To find out the physical address of the wired or wireless adapter, you need to scroll down and look for the values next to “Physical Address”. This will be your MAC address.
How to Choose Between a MAC Address and an IP Address
I have seen that while both MAC addresses and IP addresses are crucial for network communication, they serve distinct functions. MAC addresses are immutable identifiers tied to hardware, whereas IP addresses are more flexible and can change depending on the network environment.