How to View Incognito History on Android Phone
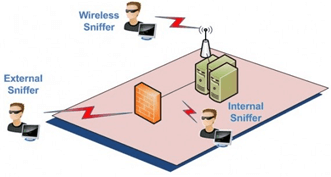
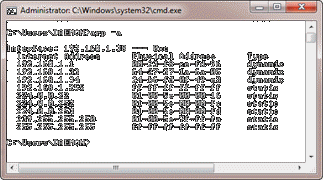
People worldwide use incognito mode on mobile browsers to avoid keeping history. According to service providers, your entries and the websites you visit in an incognito window are not recorded. However, there are a few ways to see incognito history on your phone. Moreover, you can even see another person’s incognito search history without access…